Very cool technology -- RFID and privacy
Radio
Frequency
IDentification 'tags' are used a lot. They have worked out standards so you can query a whole shipping pallet and receive the unique IDs from each package on that pallet.
The technology works by flooding the area with a low frequency radio wave.
Antennas on the RFID unit receive this radio, convert it into electricity and use this electricity to power a small transmitter which broadcasts a unique signal at a different frequency.
Obviously, due to the small amounts of power involved, these only work over a maximum distance of thirty feet or so.
Heads up: RFID tags cannot be read by orbiting satellites -- for those who think differently, check this site out:
AFDB
There are some serious privacy issues though -- someone who buys an item tagged with an RFID chip might want to render it useless after purchase but the retail store might want to scan it in the event of a warranty issue or product return.
IBM has come up with a wonderful and simple solution.
Check out this paper (PDF file) on their
Clipped Tag
Privacy-Enhancing Radio Frequency Identification Tag: Implementation of the Clipped Tag
Introduction – Enhanced Privacy for Item-level RFID
As the implementation of radio frequency identification, RFID, tagging of pallets and cases for the retail supply chain proceeds, attention is being given to the possibility of RFID tagging for individual retail items. The sale of tagged retail goods gives rise to measures to enhance consumer privacy. Ultra-high frequency tags may be read by wireless means of distances up to around 30 feet (10 meters). High frequency tags also may be read wirelessly, but generally at a shorter range.
Mechanisms have been proposed to address enhanced consumer privacy upon the introduction of item-level tagging. One of them is the use of “Blocker Tags” proposed by RSA Laboratories, a security and privacy organization. These tags interfere with the reading of other RFID tags. They must be carried by the consumer. Another mechanism is the EPCglobal Gen2 protocol “Kill” command which deactivates tags permanently. The Kill command is executed by the retailer at the point-of-sale. Killed tags cannot be revived.
The privacy-protecting tag, called the “Clipped Tag” has been suggested by IBM as an additional consumer privacy mechanism. The clipped tag puts the option of privacy protection in the hands of the consumer. It provides a visible means of enhancing privacy protection by allowing the transformation of a long-range tag into a proximity tag that still may be read, but only at short range – less than a few inches or centimeters. This enables later use of the tag for returns or recalls.
The clipped tag proposal suggests ways in which a portion of the antenna may be removed by a consumer after the point-of-sale. Figure 1 shows a schematic of the tag. A notch or slit has been placed on the edge of the plastic film, providing a means for tear initiation, similar to the slits placed in ketchup packets or snack-food bags. The tear may be directed by the use of additional perforations. The result of the tear is to remove a portion of the antenna.
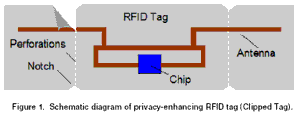
Of course, the manufacturer could always cheat and route the antenna to a non-tear area of the tag and even throw in a bit of tinfoil in the tear area to 'reassure' the customer but this overall idea looks like it will work well. Clever implementation for a valid privacy concern.
Posted by DaveH at July 13, 2006 9:30 PM
